Owen McCusker, Benjamin Gittins, Joel Glanfield, Scott Brunza and Stephen Brooks .The Need to Consider Both Object Identity and Behavior in Establishing the Trustworthiness of Network Devices within a Smart Grid. Cyber Security and Information Intelligence Research Workshop, Oak Ridge, Tennessee, April, 2010.
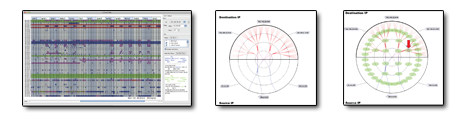
Chris Smith, Stephen Brooks, Teryl Taylor, Diana Paterson, Joel Glanfield, Carrie Gates, and John McHugh. FlowBurst & FlowCal: Interactively Visualizing Network Security Data Using Radial Diagrams and Pattern Analysis. Flocon 2010, New Orleans, Louisiana, January, 2010.
Joel Glanfield, Diana Paterson, Christopher Smith, Teryl Taylor, Stephen Brooks, Carrie Gates, and John McHugh. FloVis: Leveraging Visualization to Protect Sensitive Network Infrastructure. To appear at the Symposium on Information Assurance and Cyber Defence, Turkey, April 26, 2010.
(PDF)
Chris Smith, Stephen Brooks, Teryl Taylor, Diana Paterson, Joel Glanfield, Carrie Gates, and John McHugh. FlowBurst & FlowCal: Interactively Visualizing Network Security Data Using Radial Diagrams and Pattern Analysis. Flocon 2010, New Orleans, Louisiana, January, 2010.
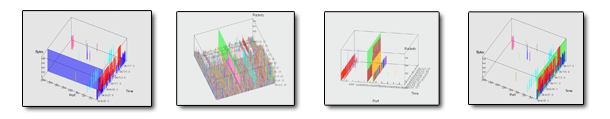
Diana Paterson, Joel Glanfield, Chris Smith, Teryl Taylor, Stephen Brooks, Carrie Gates and John McHugh. FloVis: Flow Visualization System. USENIX, Montreal, August, 2009 (Image).
Joel Glanfield, Stephen Brooks, Teryl Taylor, Diana Paterson, Christopher Smith, Carrie Gates, and John McHugh. Visualizing Properties of Network Hierarchies within the FloVis Framework. To appear in Proceedings of VizSec 2009, Atlantic City, New Jersey, October, 2009.
(PDF)
Teryl Taylor, Diana Paterson, Joel Glanfield, Carrie Gates, Stephen Brooks, and John McHugh. FloVis: Flow Visualization System. Proceedings of CATCH 2009, Washington, DC. March 3-4, pp.186-198, 2009.
(PDF)
Diana Paterson, Teryl Taylor, Stephen Brooks, Joel Glanfield, Carrie Gates, and John McHugh. Activity Plots: A Multi-entity Time Series Visualization. To appear at Flocon 2009, Scottsdale, AZ, January, 2009.
Teryl Taylor, Stephen Brooks, Joel Glanfield, Diana Paterson, Carrie Gates, and John McHugh. FLOVIS: A Netflow Visualization Tool. To appear at Flocon 2009, Scottsdale, AZ, January, 2009.
Teryl Taylor, Stephen Brooks, Joel Glanfield, Diana Paterson, Carrie Gates, and John McHugh. NetBytes Viewer: An Entity-based Visualization Tool. To appear at Flocon 2009, Scottsdale, AZ, January, 2009.
Teryl Taylor, Stephen Brooks and John McHugh. NetBytes Viewer: An Entity-based Netflow Visualization Utility for
Identifying Intrusive Behavior. In Goodall et al. (eds.),
Mathematics and Visualization (Proceedings of VizSEC), Springer-Verlag, August, 2008
Brooks-VizSec-2008
(PDF).
Teryl Taylor, Stephen Brooks and John McHugh. An Entity-based
Netflow Visualization Utility for Identifying Intrusive Behavior (Poster).
Recent Advances in Intrusion Detection, Queensland, Australia, June 2007
(Image).